Network Security
Two rules of network security:
- You can never prove you are secure. However, you can reduce risk.
- Security is always a balance between convenience and security.
Server hardening
This is about reducing the attack surface on each server so find an article from a reputable source on server hardening and follow it. Use intelligence, decision and testing in applying the hardening. Remove any roles or features not needed by the server for its job. Disable any services that are not required, for example the print spooler service is not required on most application servers. Don’t install any software that is not actually needed, like management tools when they are managed from a jump box or install utilities “because we put them on all our servers”. Be very aware that some software agents are a little too much like the spyware of “big data” for my comfort.
This reduces the attack surface on the server leaving the malware less to work with.
You might want to use WireShark on machines every so often just to see where they are sending data. Uninstall it when you finish your investigation.
How private is Microsoft software?
Microsoft’s business model has moved from a business that sells software to one that also sells user data. To reduce Microsoft surveillance, and you don’t want to transition to Linux, then have a look at these web sites to reduce the Microsoft surveillance.
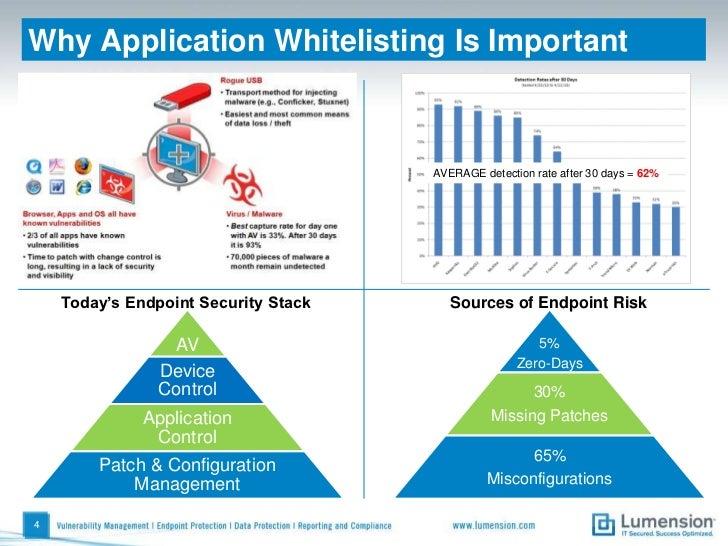
Whitelisting of servers
What is whitelisting and is it better than anti-virus? Think of anti-virus like a night club where any member of the public can enter except know trouble makers. The doorman has a blacklist and all others are given the benefit of the doubt. You only find out about a previously unknown troublemaker when they get rowdy inside.
Whitelisting entry is via invitation only. You are on the guest list of know good people or you don’t get in.
On a tightly whitelisted server only verified software is allowed to run. If a piece of malware finds it way on and tries to execute, the whitelisting software shuts the process down immediately and logs the event.
Whitelisting desktop computers can have its challenges with user expectations, but your server room is a much more controlled and I recommend tightly whitelisting all servers.
Whitelisting software you might want to evaluate include:
- Microsoft AppLocker (a free included feature with Windows server.)
- McAfee Application Control
- VMware Carbon Black Application Control
- Symantec Endpoint Protection Whitelisting.
Web application firewalls
Here is a really well written description of a Web Application Firewall by Crowdstrike:
A Web Application Firewall (WAF) is a security device designed to protect organizations at the application level by filtering, monitoring and analysing hypertext transfer protocol (HTTP) and hypertext transfer protocol secure (HTTPS) traffic between the web application and the internet.
A WAF acts as a reverse proxy, shielding the application from malicious requests before they reach the user or web application. Part of a comprehensive cybersecurity strategy, a WAF helps protect the organization from a variety of application layer attacks, including Cross Site Scripting (XSS), SQL injection, Zero Day attacks, and Denial of Service (DoS)/Distributed Denial of Service (DDoS) attacks.
A WAF differs from a network firewall in terms of the type of protection it provides and how that security is applied. Put simply, a WAF protects the organization at the application level by analysing all HTTP/HTTPS communication, whereas the network firewall acts as a barrier that prevents unauthorized access to the network on a whole.
On a technical level, the key difference between a WAF and a traditional firewall pertains to where the operational layer of security is applied as defined by the Open Systems Interconnection (OSI) model. WAFs protect from attacks at OSI model Layer 7, or the application level. Network firewalls operate at OSI model Layers 3 and 4, which focus on data transfer and network traffic.
From Crowdstrike: https://www.crowdstrike.com/cybersecurity-101/web-application-firewall/
I was checking the price on some Web Application Firewalls for a design. Some are horrendously expensive so if you are doing architecture check the prices before making your recommendations.
Monitor your firewall
How many times have I seen firewalls with any-to-any rules enabled on them? “But I needed that to make some-program work.” All too common. Firewalls have to be monitored regularly for suspicious behaviour. What is all this FTP traffic to Russia?
You need people who really know what they are doing to configure and monitor these things.
Segment your network and firewall your datacentre
Think about your user base. Some of them are “brave” clicking on links in emails from unknown sources (or a spoofed e-mail from a manager to them), installing software they have downloaded from the Internet and clicking yes to run a macro any time a document asks for it. Some user want to connect their own devices and you have no idea what is installed. Any of these actions open the door to malware resulting in the loss of intellectual property, personal information on your customers, or destruction of data. In the worst case it could bring fines and loss of reputation against the company, even criminal charges against directors.
It is a really good idea to segment your LAN with VLANs and put your datacentre behind a firewall. Treat your user’s computers as nothing more than semi-trusted.
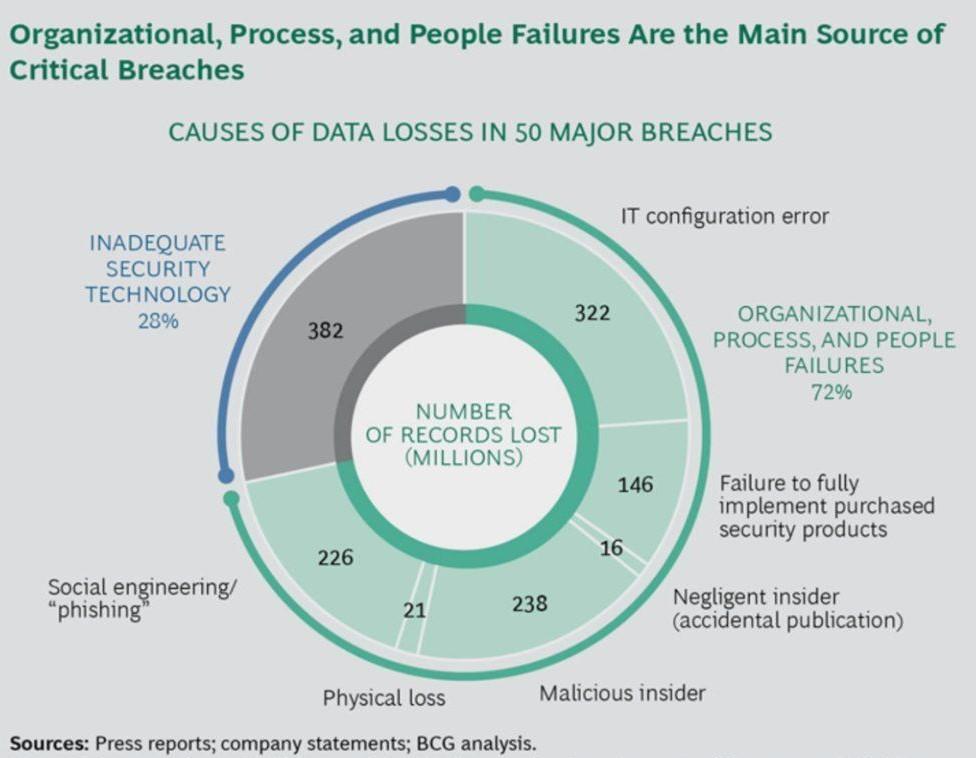
I don’t know how accurate the chart below is but it rings true to my experience. Look at how many of the data breaches were preventable through good procedure and properly trained people.
Timely patching
So often I see product managers unwilling to patch computers because the patch “might break something”. It is certainly true there are potential risks but it is a balancing of risks. Once a vulnerability is exposed it alerts the potential attackers of something they can exploit and the risks start rising rapidly.
It is essential to have a timely testing and roll out of new patches. And remember all security patches need to be installed. Don’t let administrators become selective about what patches get installed.


 Source:
Source: